Courses
Visit below to learn more about the various courses I taught while at West Point:
CS485: Ethical Hacking, CS482: Cybersecurity Engineering, IT305: Network Engineering, CY355: Cyber Foundations: Computing, and IT105: Introduction to Computing and IT.
CS485 - Special Topics in Computer Science: Ethical Hacking
- Description (from Course Catalog):
This course provides in-depth study of a special topic in computer science not offered elsewhere in the USMA curriculum. Course content will be based on the special expertise of the visiting professor or a senior computer science faculty member. - Description (Ethical Hacking):
This course provides an in-depth study of offensive tools and techniques to learn how to compromise computer networks and systems with the end-state of better understanding the various attack vectors in order to build more defensible systems. In terms of implementation, this course is primarily a guided journey through Offensive Security’s Penetration Testing with Kali Linux (PWK) course and is split into 3 blocks. The first block focuses on the provided material and exercises that lay the foundation for a successful penetration test. In this block, you will learn how to conduct information gathering (scanning), vulnerability analysis, exploitation (i.e. buffer overflows and command injection) and post-exploitation (i.e. privilege escalation, password attacks, and pivoting). The second block is then an open-ended dive into the immersive (50+ machine) PWK public lab. The final block consists of one of two capstone projects (depending on the ability of the student) to demonstrate mastery and the ability to apply these offensive skills to improve defensive systems. - Course Resources:
- Course Documents:
- Offensive Security (Jim O’Gorman) Visit Report
- End of Year Competition Poster
- 2018 Course Website - Warning: Images / Notes removed to protect PWK copyrighted content
- 2017 Course Website - Warning: Images / Notes removed to protect PWK copyrighted content
- Semesters as Course Director:
- AY 18-2 (Spring 2018) - 1 section, 12 students
- AY 17-2 (Spring 2017) - 1 section, 6 students
- Semesters Taught:
- AY 18-2 (Spring 2018) - 1 section, 12 students
- AY 17-2 (Spring 2017) - 1 section, 6 students
CS482 - Cybersecurity Engineering
- Description (from Course Catalog):
The focus for this course is to design, build and test secure networked computer systems. Topics covered include operating system and network security, secure network architecture, and offensive and defensive information operations. Practical exercises that give students hands-on experience with current network security tools and techniques complement a series of laboratory exercises that have small groups of cadets secure their own small network. In a culminating exercise, cadets design, build and test defensive measures to protect a production network from intrusions. - Course Resources:
- Semesters as Course Director:
- AY 18-2 (Spring 2018) - 4 sections, 62 students
- AY 18-1 (Fall 2017) - 3 sections, 52 students
- Semesters Taught:
- AY 18-2 (Spring 2018) - 2 sections, 29 students
- AY 18-1 (Fall 2017) - 2 sections, 31 students
- AY 17-2 (Spring 2017) - 1 section, 14 students
- AY 17-1 (Fall 2016) - 1 section, 10 students
IT350 - Network Engineering and Management
- Description (from Course Catalog):
This course addresses the analysis, design, building, and testing of modern computer networks. Network implementation techniques and considerations are discussed and practiced extensively. Key concepts include analysis and design using standardized network models, protocols, and practices such as the Open Systems Interconnect (OSI) network model, subnetting, static/dynamic routing, switching, and access control. Practical skills implementing network designs are also reinforced through several hands-on laboratory exercises using commodity network hardware. - Course Resources:
- Semesters Taught:
- AY 18-1 (Fall 2017) - 1 sections, 16 students
CY355 - Cyber Foundations: Computing
- Description (from Course Catalog):
Provides a more in-depth study of computing for cadets who have demonstrated ability beyond the level of CY305. The course covers material presented in CY305 at an accelerated pace to provide cadets additional opportunities for application and hands-on experience with cyber principles and concepts such as encryption and machine learning, with less emphasis on networking. - CY305 Description (from Course Catalog): This course builds on the foundations of Information Technology (IT) acquired during the first two years of cadet experiences to ensure graduates have the capacity and confidence to employ information technology–hardware, software, and networks–to empower people and organizations to acquire, manage, communicate, and defend information, solve problems, and adapt to change. It provides a deeper understanding of sensor and communications technologies; computer processing, storage, and networks; cyberspace operations, planning and management; interaction of IT components; IT-enabled decision making; and the evolving legal and ethical framework surrounding use of IT and operating in the cyber domain. Information Assurance issues are addressed throughout the course. Cadets complete projects throughout the course using specified information systems to meet given requirements.
- Course Resources:
- Semesters Taught:
- AY 17-1 (Fall 2016) - 2 section, 33 students
IT105 - Introduction to Computing and Information Technology
- Description (from Course Catalog):
This course addresses the analysis, design, building, and testing of modern computer networks. Network This course provides an introduction to the principles and practices of computing and information technology. The course presents foundational program design and construction techniques, with consideration given to principles of software engineering. Problem solving using computing devices as tools is a central theme throughout the course as students employ various design methodologies. Students utilize an integrated development environment and contemporary application software. Emphasis is placed on critical thinking, creativity, and learning how to learn. Students are introduced to legal, ethical, professional, and security issues and the challenges, opportunities, and attributes of the cyber domain. - Course Resources:
- Semesters Taught:
- AY 17-2 (Spring 2017) - 1 section, 17 students
- AY 16-2 (Spring 2016) - 4 sections, 67 students
- AY 16-1 (Fall 2015) - 4 sections, 68 students
Coaching
Below you will find a brief description of the cyber teams I coached including the Cadet Competitive Cyber Team as well as the teams for the Collegiate Cyber Defense Competition, Cyber Defense Exercise, and NSA Cyber Exercise.
Cadet Competitive Cyber Team (C3T)
-
Description: The C3T is a competitive academic team within the Department of Electrical Engineering and Computer Science. The team’s primary mission is to prepare for, and compete in, undergraduate cybersecurity competitions in order to improve their own computer and network security skills and to conduct outreach for the Army Cyber Center, the EECS Department, and USMA. The team competes primarily competes in Capture the Flag (CTF) competitions with undergraduate only competitions (like NYU’s Cybersecurity Awareness Worldwide CTF and UConn’s CyberSeed) as well as the various DEFCON CTF qualifiers like HITCON and Plaid.
-
Websites and Resources:
-
Semesters Coached:
- AY 18 (Fall 2017 and Spring 2018)
- AY 17 (Fall 2016 and Spring 2017)
Collegiate Cyber Defense Competition (CCDC) Team
- Description:
CCDC is a tiered competition system (state, regional, nationals) that exercises both technical and business skills. CCDC focuses on the operational aspects of managing and protecting an existing “commercial” network infrastructure. Your team will be securing, managing, and maintaining a small business network – responding to business tasks called injects, a live Red Team that is attempting to break into your systems, and maintaining a core group of “critical services” such as a mail server, e-commerce site, etc. [extracted from the CCDC team prep guide]. - Websites and Resources:
- Semester Coached:
- AY 18 (Fall and Spring 2018)
NSA’s Cyber Defense Exercise (CDX)
-
Description:
The CDX is an annual competition sponsored by the Information Assurance Directorate of the US National Security Agency which challenges a number of undergraduate institutions to design, implement, and defend a computer network against attack. The NSA builds the backbone exercise network and scoring infrastructure, acts as the competition referee, and fields a red cell with the task of compromising the confidentiality, integrity, and availability of the competitors' networks. -
Websites and Resources:
-
Semesters Coached:
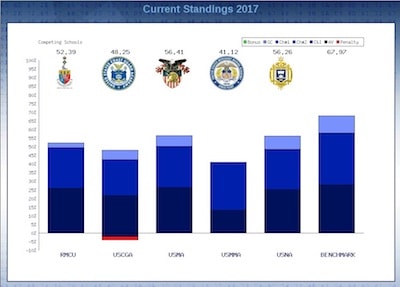
- AY 17-2 (Spring 2017)
- AY 16-2 (Spring 2016)
NSA Cyber Exercise (NCX)
- Description:
NCX is the updated CDX (started in AY18) that focuses on full-spectrum cyber operations instead of primarily defense. The exercise culminates in a three-day competition that challenges cadets and midshipmen of the U.S. Service Academies in near full-spectrum cyber operations: advancing strategic cybersecurity through education and training to develop and test their cybersecurity skills, teamwork, planning, communication, and decision-making. - Websites and Resources:
- Semester Coached:
- AY 18-2 (Spring 2018)